🟢Reversing: Baby RE
Description
"Show us your basic skills! (P.S. There are 4 ways to solve this, are you willing to try them all?)"
and we have a file, which by unzipping we give a file without extension called "baby"
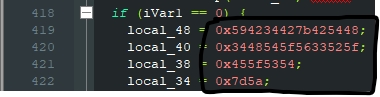
seeing the strings of this file we see an interesting thing, like
HTB{B4BYH
_R3V_TH4H
TS_Ef
"Don't run "strings" on this challenge, that is not the way!!!!"
insert key:
abcde122313but for me what most caught my attention were the following strings
puts
stdin
strcmp
GCC: (Debian 9.2.1-8) 9.2.1 20190909
baby.cbecause it indicates that this file is a file that can be decompiled into a C file
for this, I used the reverse engineering program called Ghidra
after decompiling and recompiling this program in a C code, we have this:
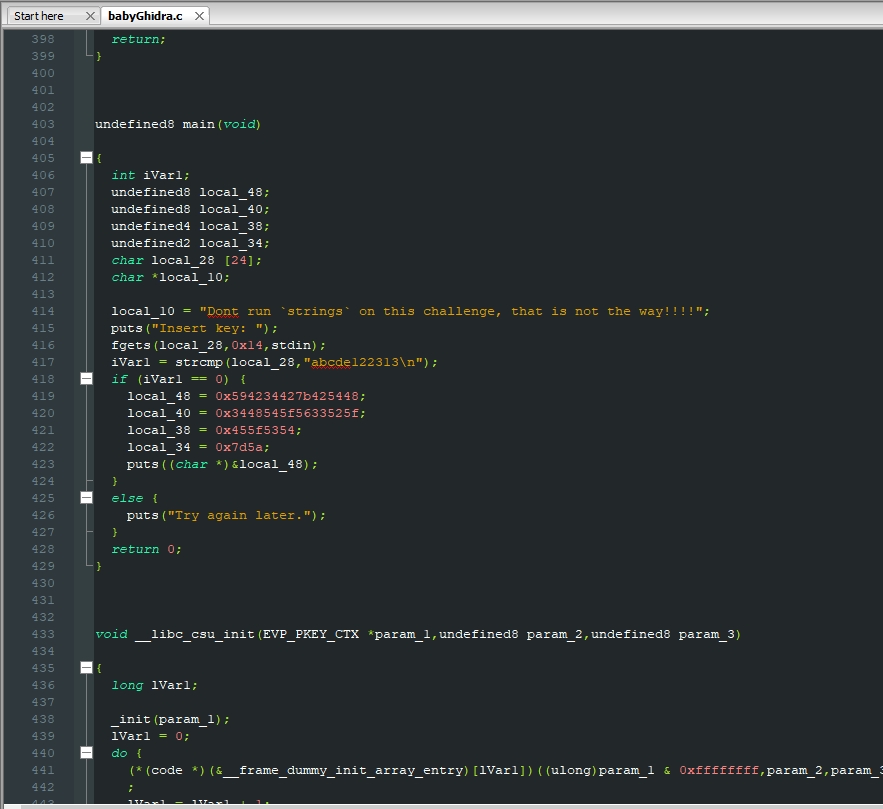
and passing these strings from hexadecimal to ASCII
we have :
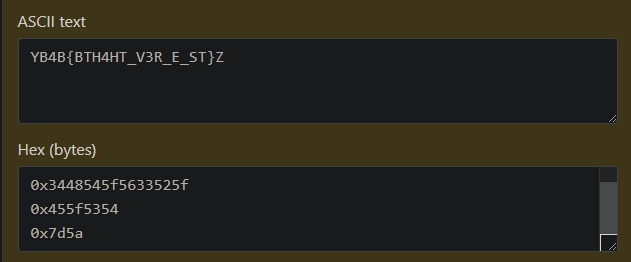
is strange because it refers to memory addresses, that is, these strings are backward, but in pairs
example : 0x7d5a is 0x5a 0x7d
then fixing, we have:
==>
now, if we convert this from hex to ASCII, we have the right flag
Last updated